Cyber Physical Systems represent a remarkable fusion of digital and physical systems, offering intelligent applications across diverse industries. CPS are characterized by their dynamic nature, where the physical world seamlessly interfaces with computing, communication, and control systems.
These innovations have spurred groundbreaking advancements in sectors like autonomous vehicles, smart cities, and industrial automation, reshaping our interactions with the surrounding environment.
CPS harnesses real-time data, sensor networks, and sophisticated algorithms to optimize performance, enhance safety, and boost efficiency.
This blog will help readers to know about the definition of cyber physical systems with their design elements, factors, security threats, and applications. The post will also discuss how it differs from IoT.
What is a Cyber physical system?
A cyber-physical system is a term used to describe fully integrated applications across hardware and software, allowing them to complete well-defined functions.
In it, computational, physical, and cyber systems are integrated and interact with each other to share data and feedback. It aims to improve efficiency, safety, and security by monitoring and controlling physical processes using data from sensors and computers.
Design
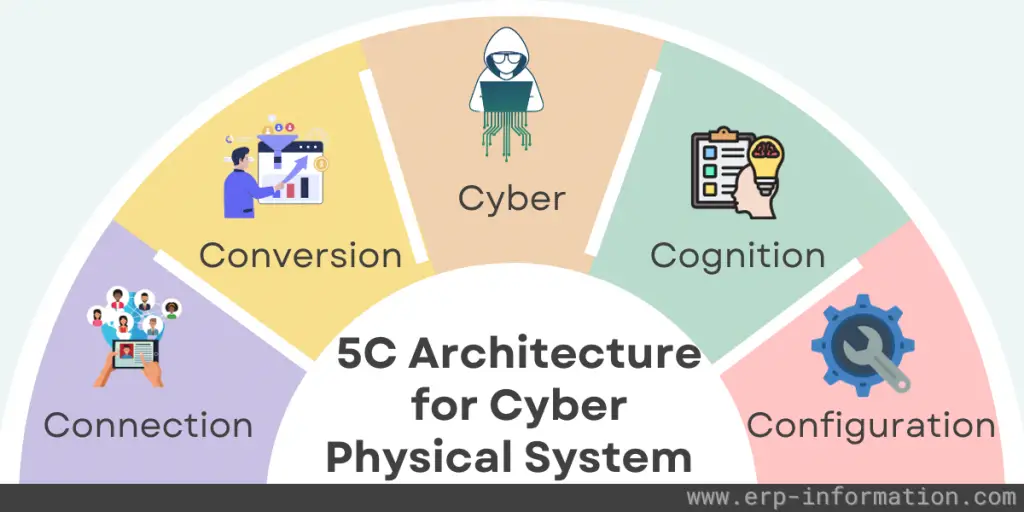
Let us discuss 5C architecture for a cyber physical system.
- Connection – Devices can autonomously connect and monitor their activity.
- Conversion – Collected data from self-connected devices and sensors are assess the qualities of pressing issues with self-awareness capabilities, allowing machines to utilize this knowledge to anticipate possible problems.
- Cyber – Every device creates its own “clone” by using instrumented features and a few procedures to more accurately portray the status of the machine. For further analysis, this generated “clone” can compare itself with other machines to assess performance.
- Cognition – Users will get a visual representation of potential issues through self-assessment and evaluation through an “infographic” that provides critical information about both the content and context.
- Configuration – By considering the priority and risk criteria, the production system can be customized to ensure performance
Design elements
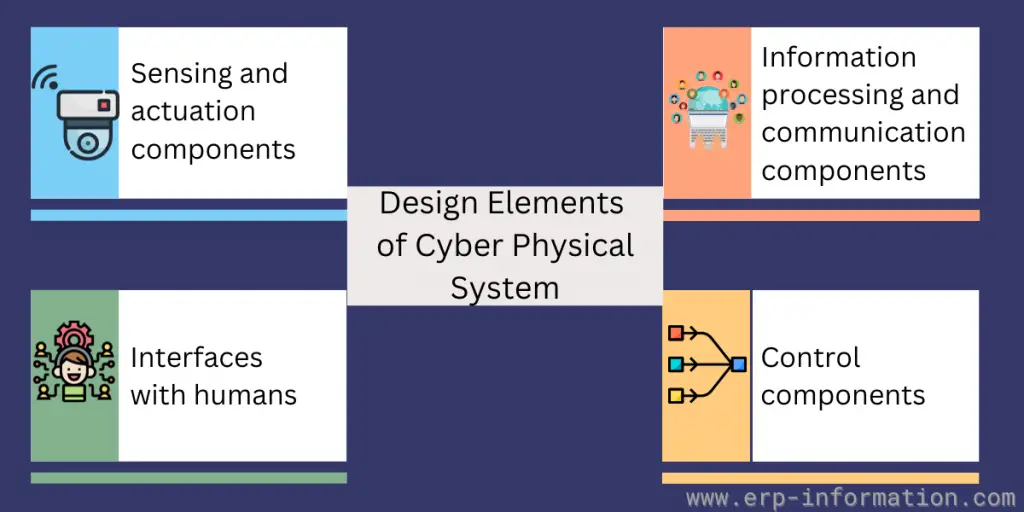
Common design elements of CPS include sensing and actuation, information processing and communication, control, and human interfaces.
Sensing and actuation components
Sensing and actuation components allow a CPS to interact with the physical world. That could involve embedded sensors that measure parameters like temperature or pressure.
The data collected by these sensor networks must be processed and communicated to other parts of the system, so that appropriate decisions can be made, for example, turning a heater on or off in response to changes in temperature.
Information processing and communication components
These are necessary to decide how to actuate on the physical system. For example, that could involve an embedded processor that runs algorithms to make decisions based on sensor data.
The processed data must then be communicated to other parts of the system to take appropriate actions.
Control components
Control components ensure that the system behaves as intended. That could involve a controller that regulates the flow of information and controls the system’s actuation.
The control component must be designed to ensure that the system meets its objectives while considering uncertainties in the physical world.
Interfaces with humans
Allow people to interact with the information system. That could involve a graphical user interface that enables users to monitor the system and input commands.
Again, it is essential to consider how users will interact with the system to ensure that it is easy to use and understand.
CPS design factors
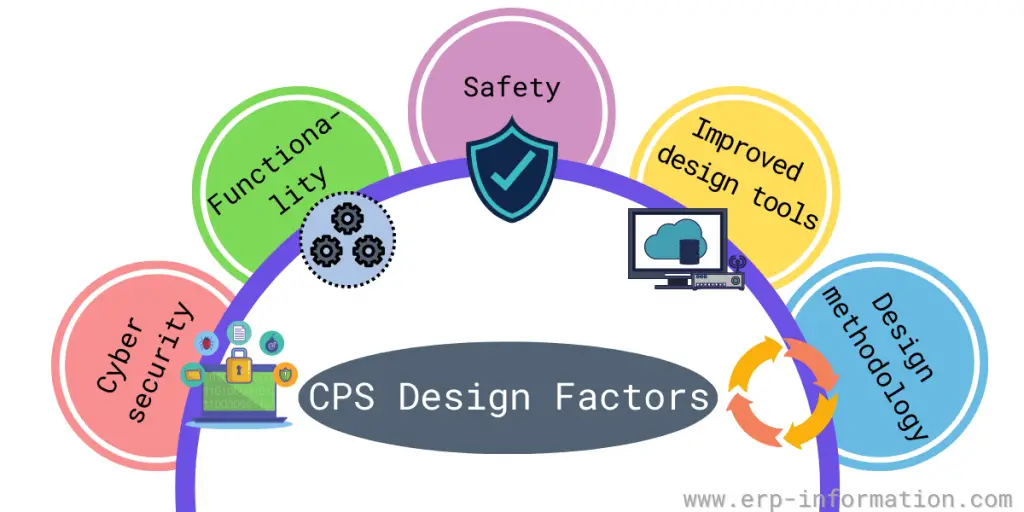
When designing, it is vital to consider the following factors:
Cyber security
Cyber security is critical when designing a CPS, as attackers often target these systems. It involves resilience, Detection, Protection, and response to unauthorized access or activities that could harm the system.
Functionality
It must be designed to meet the specific requirements of the application area. For example, a system for a smart grid must be designed to collect and process data from the electrical grid to improve its efficiency.
Safety
Safety is another important consideration when designing a CPS, as these systems often control safety-critical systems. It includes identifying potential hazards, minimizing the risk of accidents, and responding to emergencies.
Improved design tools
Improved design tools can help reduce the cost and time required to design it. In addition, these tools can provide a way to generate code, verify designs, and test systems automatically.
Design methodology
A well-defined design methodology can help ensure that it is designed correctly. That includes specifying the system’s requirements, designing the system, and testing the system.
Security threats
There are several security threats associated with CPS, including:
- Unauthorized access- This could allow attackers to access and control the system. It can be avoided by using authentication and authorization mechanisms.
- Data tampering- This could allow attackers to modify the data being collected by the system. It can be avoided by using digital signatures and cryptographic techniques.
- Denial of service- This could prevent the system from being able to collect data or perform its intended functions. That can be prevented by using security mechanisms such as intrusion detection and prevention systems.
Applications
Smart grids
The Smart Grid is a type of CPS that uses information and communication technologies to gather and analyze data from power plants, electricity transmission, distribution systems, and consumers to improve the electrical efficiency, reliability, and security grid.
Autonomous vehicles
Are designed to operate without the need for a human driver. Instead, these vehicles use a variety of sensors, such as radar and cameras, to navigate the road. They also use computer algorithms to decide when to brake, turn, and accelerate.
Aerospace systems
Aerospace systems like aircraft, satellites, and missiles use cyber systems in sensors, control algorithms, and communication systems to improve the safety and efficiency of these systems.
Medical systems
Medical systems are CPS used for diagnosis, treatment, and disease prevention. These systems can monitor patients, detect errors, and provide decision support.
Building control systems
These systems use cyber methods to manage buildings’ heating, ventilation, air conditioning, and lighting. They use sensors, actuators, and control algorithms to improve the efficiency of these systems.
Challenges of Cyber Physical System
Cyber physical systems are faced with numerous complex challenges that require constant innovation and unwavering attention.
These challenges arise due to the ever-changing nature of cyber threats in today’s intricate digital landscapes. Some of the prominent challenges include:
Sophisticated Cyber Threats
Cyber adversaries consistently refine their tactics, deploying advanced malware, zero-day exploits, and covert attack vectors. This necessitates an ongoing need for adaptation and the development of novel defense mechanisms.
Data Privacy and Compliance
Stringent data protection regulations like the General Data Protection Regulation and the California Consumer Privacy Act mandate robust security measures to protect sensitive information. Ensuring compliance with these ever-evolving regulations poses a complex challenge.
Cloud Security
With the increasing adoption of cloud-based services, the security of data and applications in the cloud becomes paramount. This requires robust identity and access management, as well as secure configuration practices.
Internet of Things (IoT) Vulnerabilities
The proliferation of IoT devices creates numerous potential entry points for cyberattacks. Ensuring the security of these diverse and often resource-constrained devices presents a significant challenge.
Insider Threats
Malicious or negligent actions by employees and insiders can pose a substantial security risk. Detecting and mitigating these threats while fostering a culture of trust requires a delicate balance.
Supply Chain Attacks
Cybercriminals increasingly target the supply chain, seeking to compromise software and hardware during development, manufacturing, or distribution. Securing the entire supply chain is a formidable task.
Threat Intelligence and Attribution
Attributing cyberattacks to specific actors or nation-states often proves elusive. A deficiency in comprehensive threat intelligence hampers the effectiveness of defense strategies.
Resource Constraints
Many organizations face budget and resource limitations in their cybersecurity endeavors, making it challenging to implement comprehensive security measures.
Security Awareness and Education
Human error remains a leading cause of security breaches. Ensuring that employees are well-informed and vigilant constitutes an ongoing challenge.
Zero-Day Vulnerabilities
Identifying and mitigating zero-day vulnerabilities, which remain undisclosed to the public and vendors, necessitates a proactive approach to recognize and address these threats.
Difference between Cyber Physical Systems and IoT
There is a considerable debate in the tech community about which is better, Cyber Physical Systems or the Internet of Things (IoT). While both have their merits, some key differences make one preferable over the other. Here’s a breakdown of each technology and how they compare.
| Cyber Physical Systems | IoT |
| Embedded systems that interact with the physical world. That could be anything from a fitness tracker to an industrial control system. | IoT is a network of devices connected to the internet. These systems can be anything from home appliances to industrial machines. |
| For example, if you wear a fitness tracker, it would use sensors to track your heart rate and steps taken and then use this data to give you feedback on your progress. | For example, if you had an IoT-enabled washing machine, it could use sensors to track the amount of laundry in the machine and then use this data to adjust the washing cycle accordingly. |
| Often, a graphical user interface allows users to input commands and monitor the system. | IoT devices often do not have a graphical user interface. |
| It controls safety-critical systems, such as power plants and nuclear reactors. | IoT devices are used for less critical applications, such as controlling home appliances. |
FAQs
What is Cyber Physical Systems Research?
It studies systems where computation and physical processes are integrated and interact with each other to create intelligent, behavior-rich systems.
What is the role of the National Science Foundation in CPS?
The National Science Foundation is one of the leading funding agencies for cyber system research. It supports advances in the basic knowledge and systems to make it a reality.
How do CPS distinguish from conventional systems?
CPS are unique due to their ability to collect data from sensors, process it digitally, and make instantaneous decisions. They bridge the physical and digital domains, offering solutions that are agile and adaptable.
What are some typical applications of CPS?
It finds utility in autonomous vehicles, smart cities, industrial automation, healthcare devices, and more. It improves efficiency, enhances safety, and provides convenience across a broad spectrum of industries.
How is data security and privacy ensured within CPS?
It establishes data security by implementing robust cybersecurity measures, encryption, and utilizing secure communication protocols. Privacy is safeguarded through compliance with data protection regulations and the management of access control.
What is the connection between artificial intelligence (AI) and CPS?
Artificial intelligence (AI) and machine learning are an integral part of CPS, empowering these systems to acquire knowledge from data, adapt to changing circumstances, and enhance their performance over time. They significantly support decision-making capabilities.
How can organizations integrate CPS into their operations?
Organizations can integrate CPS by evaluating their specific requirements, selecting appropriate technologies, and collaborating with experts in the field. Pilot projects and gradual implementation are often recommended strategies.
Conclusion
Cyber Physical Systems are embedded systems that interact with the physical world. They transformed the way people interact with information and computational resources and have the potential to revolutionize many industries, such as transportation, healthcare, and manufacturing.
While it has many benefits, it also comes with some challenges, such as ensuring the security of these systems. We hope this blog post has enabled you to understand CPS and how they work.