Given that the world increasingly relies on software, it’s no surprise that risks related to vulnerabilities in software are also growing. However, there’s no need for security efforts to jeopardize development speed or deadlines.
Instead, developers play a crucial role in organizational-wide security efforts by simply being aware of and securing all code they use, including any open-source materials.
This is where the Software Bill of Materials (SBOM) comes in. It is a process that helps you manage and follow all the software in your organization.
This article will discuss SBOM thoroughly, including its definition, the minimum required elements, advantages, and disadvantages. It also gives tips for creating software bill of materials.
What is the Software Bill of Materials?
An SBOM is a comprehensive inventory of software components that assists companies in enhancing the security of their software products upon detection of vulnerabilities. Essentially, it compiles a detailed list of all the software utilized in product development, enabling swift mitigation of any security risks associated with those components.
A particular application or system is built using a detailed inventory of software components, dependencies, and related files.
It provides a way for software developers and suppliers to track the origin of each element and version so that they can reproduce it if necessary.
It also helps organizations manage the code quality risks and security vulnerabilities associated with using open-source software by providing a way to identify which components are open-source and which are not.
This can help prevent new vulnerabilities from being introduced into the software.
By having a software bill of materials, software companies can track which versions of a component are used in which products and show transparency and trust in the quality of their product.
Furthermore, this practice is part of good quality assurance (QA) which can give these types of businesses a competitive edge.
Organizations can better manage risk and ensure compliance with security and licensing requirements by understanding the relationships between different software components.
In light of the recent cyberattacks and heightened cybersecurity regulations, all software companies must begin utilizing SBOMs.
Importance of SBOM
As cyberattacks become more prevalent, the need to manage security and license compliance is expanding. That emphasizes using SBOMs as they help show the software’s quality.
On May 12, 2021, the United States issued an executive order called ‘Executive Order on Improving the Nation’s Cybersecurity.’ This order brought attention to the idea and need for SBOMs.
The wording in this executive order came from previous work done by the National Telecommunications and Information Administration (NTIA) and its Software Component Transparency project. These initiatives showed that there is a necessity for any software sold to the US government to come with an SBOM.
The heightened awareness within the private sector and regulated industries caused by this event have changed how these companies operate.
For example, Scania (part of the Volkswagen Group) now only accept software from their suppliers if an SBOM is provided.
Before, the European Union didn’t have much direction regarding cloud solutions, the Internet of Things (IoT), third-party components and libraries inventory, or SBOMs.
The executive order regarding SBOM awareness has resulted in positive global change by meeting the requirements set forth by vulnerability disclosure programs.
Because most software companies sell their products to US customers or even the government at some point, they must be cognizant of this transition towards increased SBOM usage.
The Biden-Harris Administration disclosed a fact sheet on March 21, 2022, highlighting the importance of businesses strengthening their cybersecurity measures.
The logic is twofold: first, cyberattacks are becoming more frequent; second, Russia is likely to engage in “malicious cyber activity.” Given that vulnerabilities will continue to occur (inevitable), companies must be prepared.
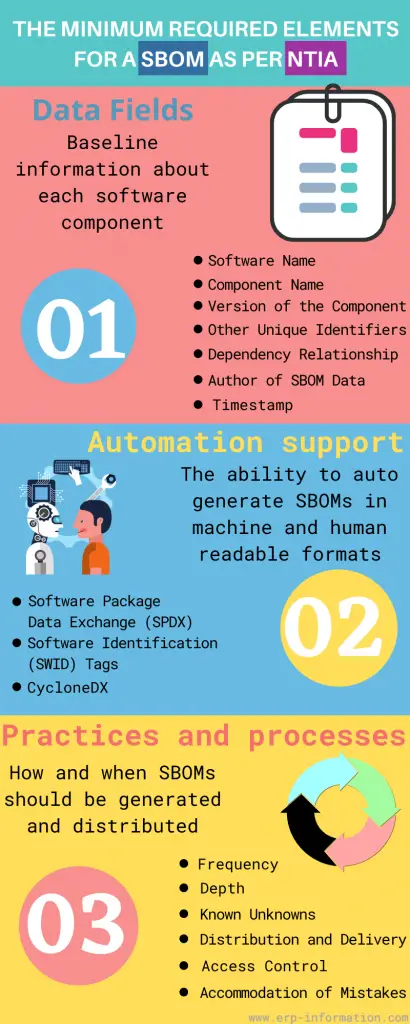
SBOM Minimum Elements
The NTIA has published the minimum requirements document to help standardize the process. For more details, refer NTIA – SBOM minimum elements report.
In this infographic, we’ll take a look at those elements.
A closer look at SBOMs
Every single component is cataloged when any form of transportation, whether an airplane or car, is built. An inventory outlines which parts were used during the production process. If a part needs to be recalled or fails, it would be immediately clear which vehicle it impacts.
The same way we keep track of individual parts when creating something also applies to developing software safely.
An SBOM lists all the ingredients used in a piece of software. This inventory includes every software component and dependency in an application, with minimum elements like data fields (name, version, license).
Most software bill of materials are open source and include any third-party software being utilized.
It contains so much data that a machine can only process it. Having a human processor or manual approach would take too long and wouldn’t be efficient.
To make sure both the provider and consumer of the SBOM can interpret the data, it must be in a format that they can programmatically read and communicate quickly to keep up with development cycles.
Today, the software business is coming together to create a standard format for inventory that considers SBOMs and automation support.
A consistent presentation of SBOMS will make it easier for software companies and consumers to use and share them easily.
Data fields
- Software name
- Software version
- Hardware name
- Hardware version
- Component name
- Component version
Additionally, the following data fields are recommended:
- A brief description of the software or hardware
- The website where you can find more information about the component
Industry-wide initiatives of note
Industry-wide initiatives of note include
CycloneDX
CycloneDX is a “lightweight” standard for SBOMs created in the Open Web Application Security Project (OWASP) community. It is meant to be used in application security contexts and supply chain component analysis.
OpenChain ISO/IEC 5230
This specification facilitates and strengthens different business use cases throughout the software supply chain.
A few examples where this standardization would benefit are procurement and outsourcing or due diligence for mergers and acquisitions (M&A) activity.
SPDX
The Software Package Data Exchange (SPDX) is an international open standard that enables the communication of software bill of material information, including components, license copyrights, and security references.
SWID
SWID tags help organizations keep track of which software is installed on devices by including information that identifies the specific release of a software product.
Why is it Integral in Securing the Software Supply Chain?
Developers need to be aware of the components used in the software supply chain, and those passed along downstream.
That includes information such as an SDK, operating system, or other modules that customers use when building applications.
In the past 12 months, Anchore’s 2022 Software Supply Chain Security Report found that software supply chain attacks have impacted nearly two-thirds (62 percent) of organizations.
The attackers and victims here are software companies who unknowingly spread vulnerabilities through their code. Therefore, it becomes crucial to identify all components used in production.
An SBOM can save time by facilitating immediate communication about vulnerabilities by knowing which components and licenses are in use.
Without this information readily available, development teams have to waste time figuring out if they’re using a vulnerable component (as with Log4j) instead of fixing the issue.
The Inclusion of SBOMs in Software Composition Analysis
Creating accurate, up-to-date SBOMs is just one part of a comprehensive software composition analysis (SCA) program.
SCA automates the process of obtaining visibility into the use of open-source software and other third-party content, supporting application security, risk management, and license compliance.
SCA can detect and follow all OSS and the licenses connected to them, creating an SBOM based on those findings.
It can also aid in constructing and upholding policies, keeping tabs on security vulnerabilities, and integrating open-source code scans into the built environment.
Automation in SCA is key for keeping up with rapidly changing development environments. Static audits can’t keep pace because new vulnerabilities arise every day. SCA’s automated updates let developers focus on what they’re good at writing great code.
How to Create a Software Bill of Materials? (Tips and Life Cycle)
The below info shows the steps of SBOM creation.
Steps of SBOM creation are:
- Define the project scope and requirements. This includes understanding the business need, defining the features and functionality, and estimating the effort required.
- Establish a timeline for the project. Include milestones and due dates for each component.
- Create a list of software components needed for the project. This should include both commercial and open-source components and any custom code that will be written.
- Assign a cost to each component. This can include licensing fees, development costs, and other associated expenses.
- Verify that all dependencies are accounted for. For example, if one component depends on another, ensure the dependent component is included.
- Validate it with all stakeholders. This includes subject matter experts, developers, and management.
- Update it as needed throughout the project. It may require changes due to new requirements or changes in scope.
Creating a Software BOM can seem daunting, but it’s essential to any software engineering project. By taking the time to develop a detailed SBOM, you can avoid costly surprises and keep your project on track.
Tips for creating an effective SBOM
- Start with a well-defined plan. Having a plan for your SBOM is critical to its success. Make sure you know what you want to accomplish and how you will go about it.
- Define your components. Each component in it should have a clear purpose and be easily identifiable.
- Keep it organized. Use a logical structure to keep it easy to navigate and understand.
- Use consistent naming conventions. Naming conventions help ensure clarity and avoid confusion among team members.
- Document everything. The more information you include, the easier it will be to implement and maintain it over time.
- Test, test, test. Ensure it is thoroughly tested before release to ensure a smooth transition into production.
By following these tips, you can create an effective Software Bill of Materials that will help you streamline your software manufacturing process.
Best practices for creating and maintaining an SBOM
The best way to protect open-source software is by taking a “shift-left” approach and incorporating compliance and security risks into the development process. By doing this, you’ll be able to keep developing software without slowing down or stopping releases.
The open source program office (OSPO) can help to create policies about using open source and also work to manage risks related to it. That includes maintaining a software bill of materials.
SBOM standards, like SPDX, help to establish what should be included in an SBOM.
Life cycle
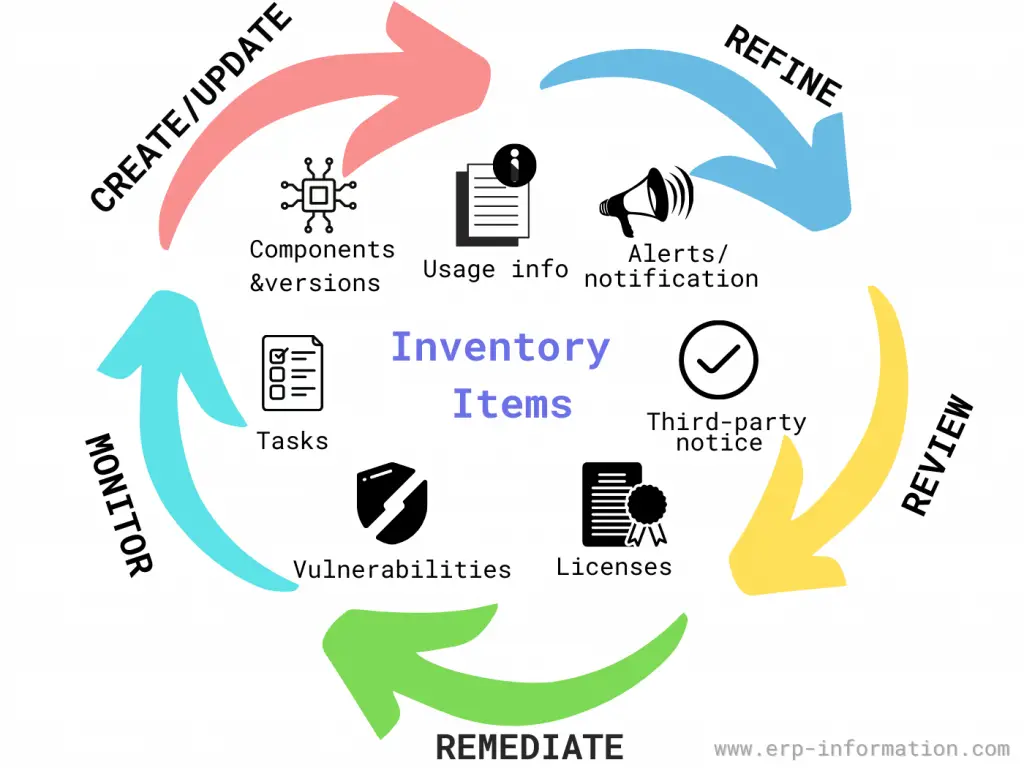
The SBOM life cycle includes the following:
- Creating (and updating) the SBOM.
- Refining it.
- Reviewing it.
- Remediation (in the case of discovered vulnerabilities).
- Monitoring for ongoing and frequent updates.
It typically contains the following:
- Software components and versions
- Software vulnerabilities
- Licenses
- Third-party notices
- Usage information
- Alerts and notifications
- Tasks
As supported by SCA with regular automation, this speeds up the code review process so that developments are updated on time.
Advantages
- Cut development time in half.
- Eliminate confusion over versions and dependencies.
- Always know what’s going into your software
- Streamline QA and testing
- More accurate estimations
- Improved collaboration
- Visibility across the organization
- Easier to change requirements
- Faster time to market
- More reliable software releases
Advantages in detail
The first benefit is that it gives customers better visibility into their software architecture and an understanding of how different system parts interact.
It also helps manage risk by providing a “single source of truth” for internal and external stakeholders who need to know about changes to the system.
It enables more efficient team communication, speeding up decision-making processes as everyone can access all relevant information. This improved collaboration results in faster turnaround times and reduced development costs.
Finally, it aids in troubleshooting and problem-solving by providing a snapshot of the system at any given time.
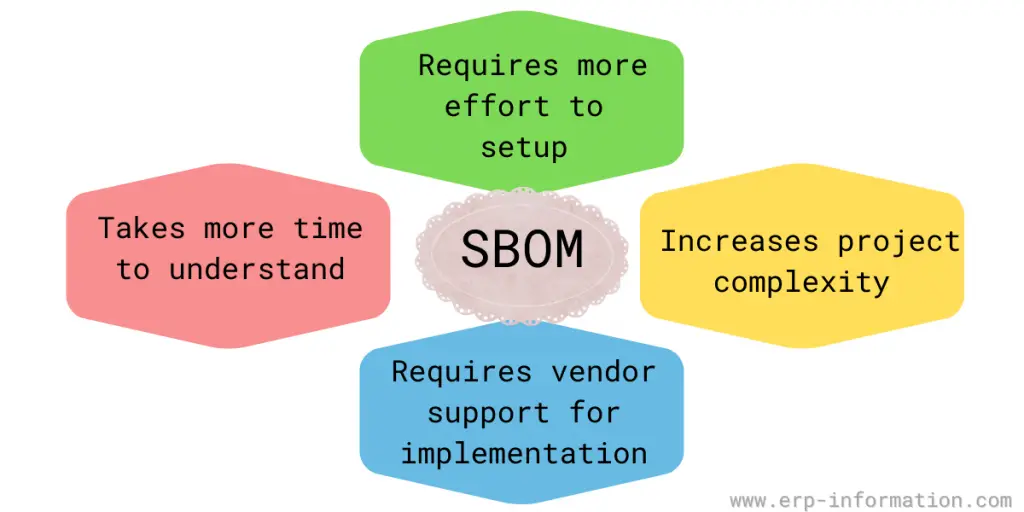
Disadvantages
- It takes time to understand because it’s too specific in details
- It requires vendor support for implementation
- It increases project complexity
- It demands more effort for setup with no shortcuts offered by SBOMs
Writing Software with Security in Mind
By managing and tracking security risks, you can prevent vulnerabilities before they’re even an issue. That will result in safer products that give you fewer headaches overall.
In addition, integrating SCA and a software bill of materials into your software development practices can automate continuous management without derailing development or releases.
If a developer needs open-source code to fill a required function or address a technical issue, they should first see if the code matches best security practices.
That will help keep out any suspect code that might have holes in its security. Also, keeping an up-to-date SBOM can help immediately identify and fix security issues with the code.
Software Bill of Materials Open Source
61 percent of codebase files were from open-source components, according to a study by Revenera. This is 6 percent more than last year. Open-source software is used a lot, but not many people know about it. Only 6 percent of issues discovered during audits were disclosed before the audit started. So, organizations need to track their open-source components better and understand the risks that come with them.
An open-source software bill of materials is a document that contains a list of the open-source components used in a software system.
It can be used for various purposes, such as understanding the license obligations for a given system and determining the copyright status of individual third-party software components. It can also be helpful for auditing and managing the code in a system.
There are a few different ways to create an SBOM. One approach is to start with the source code for the system and identify all of the open-source software components.
Another method is to use a tool such as FOSSology to scan binary executables or packaged software for open-source licenses. Once you have it, you can keep it up-to-date by tracking changes to the source code or license files.
It can be helpful for a variety of purposes, including:
- Understanding license obligations
- Determining copyright status
- Auditing/managing the software
FAQs
What is the software supply chain?
The software supply chain is a process that involves the development, distribution, and maintenance of software systems. It encompasses activities such as coding, testing, and deploying software, as well as managing dependencies and ensuring the security of the software components used in the development process.
What is software supply chain management?
Software supply chain management is the process of overseeing and controlling the various components and activities involved in the creation, development, and distribution of software. It includes managing the sourcing of software components, ensuring their security and quality, coordinating collaboration between different teams, and maintaining visibility and control over the entire software development and distribution process.
Is SBOM part of an ERP system like SAP business?
No, SBOM (Software Bill of Materials) is not typically a part of an ERP system like SAP Business.
What are software supply chain risks?
Four prominent software supply chain risks are
* Known Vulnerabilities: A known vulnerability in software supply chains is the risk of a system or component being exposed to malicious attack, disruption, or destruction due to an identified security hole. For example, third-party software can come with vulnerabilities. However, you can prevent it by using software component analysis (SCA) solutions. These solutions identify the SBOM of a given code.
* Unknown vulnerabilities: Some common mistakes happen during codings, like poor encryption, logic flaws, and memory corruption. These things make applications vulnerable.
* Non-code: Vulnerability can be found not only in code but also in binaries like EPMs, firmware, and configuration files.
* Malicious code: Finding malicious code like external injection attacks is difficult because they come up as validated components.
What is the difference between a BOM and a SBOM?
A bill of materials (BOM) is a comprehensive list of all the components and materials required to manufacture a product. A software bill of materials (SBOM) is a similar list, but specifically for software applications.
What is difference between SCA and SBOM?
SCA (Software Composition Analysis) and SBOM (Software Bill of Materials) serve different purposes in software development and cybersecurity.
SCA focuses on identifying and managing open source and third-party components used in software applications. It helps developers track and assess the security vulnerabilities and licensing obligations associated with these components.
SBOM, on the other hand, is a detailed inventory of all the components and dependencies used in a software application or system. It provides a comprehensive list of software parts, including open source and proprietary components, along with version information and relationships.
In summary, SCA is primarily concerned with analyzing and managing the security and licensing risks of software components, while SBOM provides a detailed inventory of all the components used in a software application or system.
Who needs an SBOM?
Software developers and vendors need an SBOM (Software Bill of Materials).
What is the difference between OSS and SBOM?
Open Source Software (OSS) refers to software that is openly available and can be modified, distributed, and used by anyone under specific licensing terms. Software Bill of Materials (SBOM) is a document that provides a detailed inventory of the components used in creating a software application, including open source and third-party dependencies.
Conclusion
Software Bill of Materials can be handy for managing software development projects. By taking the time to create it, you can avoid costly surprises and keep your project on track.
In addition, by using a well-defined plan, defining your components, and using consistent naming conventions, you can create an easily- navigable SBOM that will help ensure a smooth transition into production.
References: