You’ve just been handed a hefty bill of materials (BOM) for a new software system. You’re unsure where to start, and some components will be difficult to procure and integrate. Building this system from scratch is daunting, and you’re unsure where to start. For that, you need to do a software composition analysis, but you don’t know what that is or how to do it.
Software composition analysis is the process of identifying all the software components in a system and their dependencies. By understanding the composition of your system, you can make better decisions about procurement, integration, and development process.
This article discusses SCA in more detail, including its definition, working, importance, benefits, and limits. We will also provide a tool list, important things to be considered while choosing the tools, and best practices.
What is Software Composition Analysis?
It is the automated process of inspecting software for the presence of components from third-party sources and identifying the licenses associated with those components.
In addition, these tools can help you build a bill of materials (BOM) that documents your product’s software, including the licenses for each component.
Many commercial products include software from third-party sources, and it’s important to know the license compliance is associated with those components. If your product includes software licensed under terms incompatible with your own license, you may violate copyright law.
It can also help you identify security vulnerabilities that attackers could exploit. Many open-source components include known security vulnerabilities, and it’s important to know which ones are included in your product so you can address them.
How does it work?
One way these tools work is by generating a bill of materials (BOM), which lists all the software components in an application and their dependencies.
The BOM can be used to track licenses and vulnerabilities for each component. It can also help you understand how the application works, making it easier to debug and modify.
The software from third-party sources and open-source software are identified and compiled into BOM, and they are again compared with various databases, including the National Vulnerability Database (NVD). These databases store data on known and common vulnerabilities.
Comparison of BOMs with databases helps security teams to identify security vulnerabilities and fix them quickly.
Why is it important?
One important reason why this tool is important is that it can help identify vulnerabilities in open-source software code.
By identifying these vulnerabilities, organizations can take steps to mitigate the risks they pose. Additionally, It can help organizations comply with regulations such as the Payment Card Industry Data Security Standard (PCI DSS).
How do you choose the Software Composition Analysis tool?
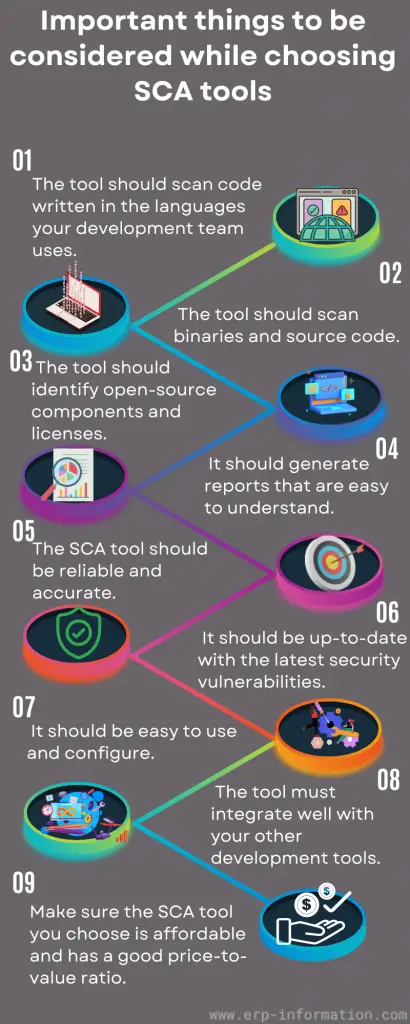
You need to consider some important things while choosing SCA tools.
- The tool should scan the code written in your development team’s languages.
- The tool should scan binaries and source code.
- The tool should identify open-source components and licenses.
- It should generate reports that are easy to understand.
- These tools should be reliable and accurate.
- It should be up-to-date with the latest security vulnerabilities.
- It should be easy to use and configure.
- The tool must integrate well with your other development tools.
- Ensure the tool you choose is affordable and has a good price-to-value ratio.
- Research the best SCA tool for your needs, and read reviews
Best practices
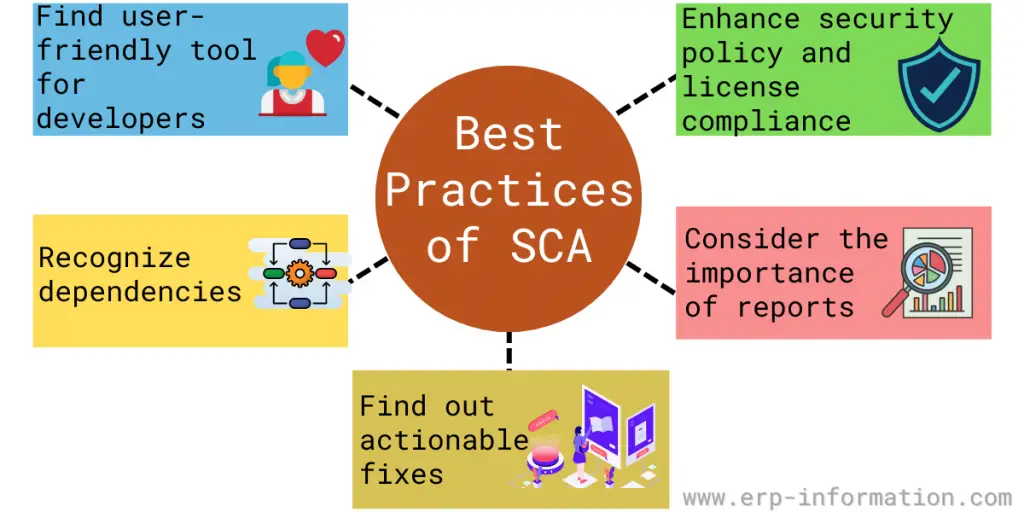
Find a user-friendly tool for developers
Developers are the persons who write codes. If the tool is not user-friendly, it slows developers’ work. Educate the developers about these SCA tools and make them understand the importance of the tool.
Recognize dependencies
There are two types of dependencies in open-source, direct and transitive or indirect. Direct dependency is a combination you use in the project, but indirect dependency is a combination that one of your dependencies used.
Most of the vulnerabilities in open source exist in indirect dependencies. Hence it is important to understand the dependencies to detect vulnerabilities easily.
Find out actionable fixes
With the help of a good SCA tool, automate the scanning process and continuously monitor code. The tool alerts you about vulnerabilities and directs you on how to fix them.
Consider the importance of reports
Always have a detailed SBOM report to track all software components when you purchase the software. And also a report on security practices and vulnerability fixes.
Enhance security policy and license compliance
Understand the open-source packages that developers use and then define security guidelines. Always keep track of open-source licenses to enhance compliance.
Future
The future of software composition analysis is bright. It is becoming increasingly important as the world relies on open-source software and increasing breaches and cyber attacks.
SCA tools are becoming more sophisticated, and the bill of materials generated by these tools is becoming more accurate. As companies become more aware of the importance of software composition analysis, the use of these tools will continue to grow.
Benefits
- Detection of vulnerable and out-of-date software
- Identification of licenses and open-source components
- Determination of the security posture of an organization
- Identification of copyright infringement
- Improved security for your organization as a whole
- Increased confidence in using third-party software components
- Faster time to market by identifying and mitigating risks early
Limitations
- It cannot identify open-source components that are embedded in proprietary software.
- A lack of comprehensive data can hinder the accuracy of results.
- It cannot detect modifications to open-source components.
- Incorrect usage of open-source components can be difficult to identify with this tool.
- Results from SCA can be time-consuming and expensive to remediate.
Software Composition Analysis tools
- GitHub
- Gitlab
- Synk
- Black Dusk
- Cast Highlight
- ThreatWorx
- ActiveState Platform
- Aqua Platform
- Wiz
- Rainforest Application
FAQs
What are the steps in software composition analysis?
The steps are:
– Identification of software components
– Evaluation of software components
– Identification of dependencies between software components
When can you use software composition analysis?
It can be used during all stages of the software development life cycle. It can help with licensing, vulnerability assessment, and other purposes.
What are the reasons for using software composition analysis tools?
The reasons are as follows.
1. To identify and manage risk: One of the most important uses is to identify components in software that pose a security risk.
2. To comply with regulatory requirements: In some industries, such as healthcare and finance, regulatory agencies require organizations to demonstrate due diligence in their software management processes. Composition analysis can help organizations meet these requirements.
3. To assess license compliance: Many software compositions contain open-source components, and it is important to understand the licensing obligations associated with their use. Software composition analysis can help you track down all the open-source components in your software and assess your compliance with relevant licenses.
4. To improve quality and mitigate defects: Open source components are often responsible for applications’ defects, so a composition analysis tool can help you find and fix these defects before they cause problems for your users or customers.
5. To get a comprehensive view of your software architecture: A well-run software composition analysis process will provide you with a complete inventory of all the software components in your application, as well as information about where they came from, what licenses they are under, and how they are used.
This comprehensive view can be extremely valuable when tracking down sources of defects or understanding the impact of changes to your software architecture.
Conclusion
Software composition analysis is the process of identifying and evaluating software components. These tools use software bill of materials to identify component dependencies, which can then be used for licensing, vulnerability assessment, and other purposes.
It is an important part of software development and management and should be considered during all stages of the software lifecycle.