Cyber threats have become more sophisticated, so organizations must ensure their networks are secure from malicious actors.
Traditional security systems like firewalls and antivirus software are no longer enough to keep your network safe. Intrusion Prevention Systems (IPS) can provide extra protection against these threats.
Integrated security system IPS is a security technology that helps protect businesses against cyber attacks.
Nevertheless, the systems work differently than the ones described above. Therefore, identifying the distinct types is crucial for understanding the differences among intrusion detection and prevention systems.
Finding the right IPS solution for your business needs is crucial, so we will list the examples of intrusion prevention systems.
The post is listed the top 10 IPS solutions available today. With this guide, you will have all the information you need to decide which intrusion prevention system is right for you.
What is an Intrusion Prevention System (IPS)?
Intrusion Prevention System (IPS) is a security system that guards a network or system against malicious activity. It works by monitoring and analyzing incoming traffic for suspicious activity, like unauthorized access attempts, malicious code, and other malicious activity.
If any suspicious activity is detected, the IPS will block it from entering the network or system.
It is also known as an intrusion detection and prevention system because IPS is examined as an augmentation of Intrusion detection systems (IDS). Both systems protect the network from malicious activities and operate network traffic.
IPS records observed events, informs security administrators of important observed events, and produces reports.
How does an IPS work?
An Intrusion Prevention System (IPS) actively monitors and analyzes an organization’s networks, systems, and applications for malicious activities like malware and scripting attacks in real time.
When suspicious activity is detected, it will immediately alert the network administrator, who can then take action to prevent further intrusion.
An IPS uses multiple methods, such as signature-based detection, protocol anomaly detection, heuristic analysis, and rate limiting, to detect malicious traffic before it can cause harm.
It also provides in-depth prevention with sandboxing technologies that allow IT professionals to analyze suspicious files without risking the safety of their system. Ultimately, using an IPS helps organizations stop cyberattacks before they occur.
Types of IPS
Two main types of IPS are
Network-based IPS (NIPS)
Network-based IPS solutions are typically deployed at the perimeter of an organization’s network and monitor inbound and outbound traffic to detect malicious attempts or suspicious behavior.
Host-based IPS (HIPS)
Host-based intrusion prevention systems (HIPS) are specialized security solutions that protect an individual host or device from malicious activity.
They analyze system-level events, like file creations and process executions, to identify potentially malicious activity. HIPS are designed to protect a single host or device, so they are usually deployed alongside other security mechanisms on-premises.
Other types are as follows.
Wireless intrusion prevention system (WIPS)
Wireless Intrusion Prevention System (WIPS) is a specialized security solution to protect wireless networks from malicious activity.WIPS uses heuristic-based technology and deep packet inspection to detect and prevent unauthorized access, man-in-the-middle attacks, and other malicious activities.
Network behavior analysis (NBA)
A security technique that examines the network traffic for malicious or policy-violating activity. It uses advanced analytics to detect and identify abnormal patterns in network behavior, such as those associated with malware, insider threats, data exfiltration, and other cyber-attacks.
Host-Based vs. Network-Based
A hosted IPS protects the specific endpoints in their network. It will monitor the traffic in and out of a computer, processes running the system, changes made to the files, etc. Networked solutions provide monitoring of the network. They usually consist of a packet sniffing tool that collects packets from the internet connection.
Techniques used by IPS to detect threats
- Signature-based detection: This system correlates activity to signatures of well-established threats. The drawback of this method is it can detect already identified attacks but not new ones.
- Statistical anomaly-based detection: This system compares network activity samples to a benchmark standard to detect abnormal behavior. It is more reliable than signature-based monitoring, although the results can occasionally be inaccurate. The most modern intrusion prevention systems leverage artificial intelligence, machine learning technology, and anomaly-based monitoring for even greater accuracy.
- Stateful protocol analysis detection: This is a less commonly used method compared to other methods. It follows enterprise security policies and does not allow activities that violate them.
Benefits of IPS
Increased security
Intrusion prevention systems provide an extra layer of security by monitoring and analyzing network traffic for malicious activity. They can detect suspicious behavior, such as attempts to access unauthorized data or networks, and alert administrators so they can take action quickly.
Improved visibility
An intrusion prevention system provides visibility into the activities occurring on your network in real time, allowing you to identify potential threats before they become a problem. That allows you to proactively address any issues and ensure your organization always remains secure.
Reduced costs
By having an intrusion prevention system in place, organizations can reduce the costs associated with responding to security incidents since they can be identified early on and dealt with quickly rather than waiting until it’s too late.
Improved Compliance
Intrusion prevention systems help organizations meet regulatory requirements by providing detailed audit trails of user activity, making it easier to comply with industry standards such as PCI DSS or HIPAA.
Enhanced Productivity
With an IPS in place, organizations benefit from improved productivity because employees can work without interruption from malicious attacks or other security threats.
Limitations of IPS
IPSs are not always perfect. They don’t have software to help with network devices or keep people from copying information. IPSs and IDSs can only stop intruders when they start to get into the network. The purpose of this system is to keep data and resources safe.
Ten best intrusion prevention systems.
1. Check Point IPS
Checkpoint intrusion prevention systems (IPS) offer organizations essential security features to protect against evading and sophisticated attackers.
Checkpoints can monitor behavior and protocol problems by detecting DNS tunnel attempts, signatureless attacks, protocol misuse, and known vulnerabilities. IPS is an integrated tool for companies deploying IPS with default and recommended policies.
Features
- Signature and behavioral preemptive protection
- Prevention from known and unknown attacks
- Outbound malware communications
- Real-time protection
- Microsoft vulnerabilities coverage
- Efficient and flexible deployment
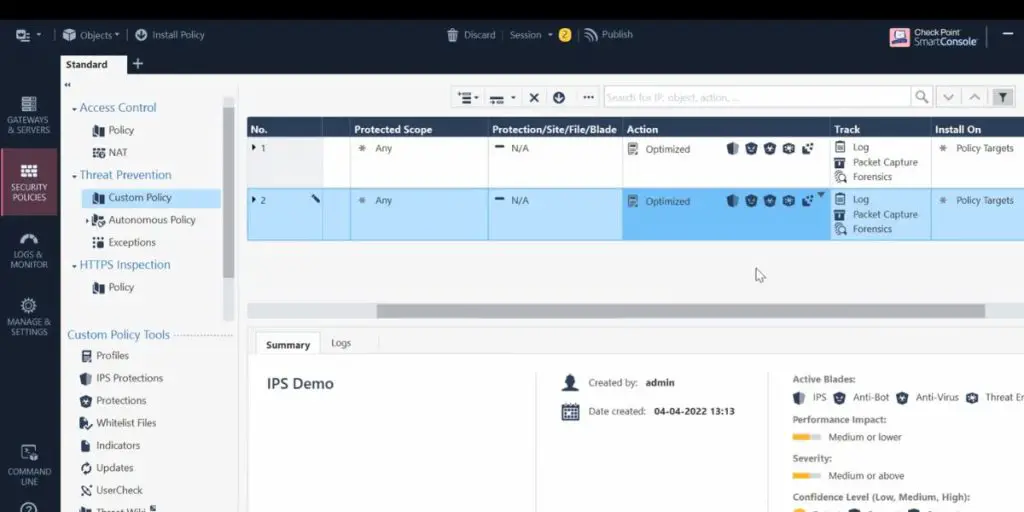
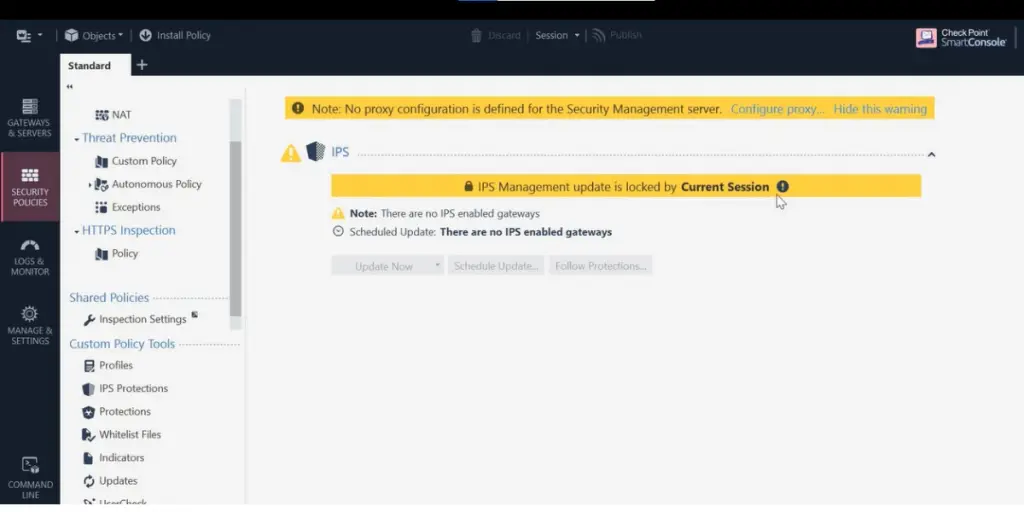
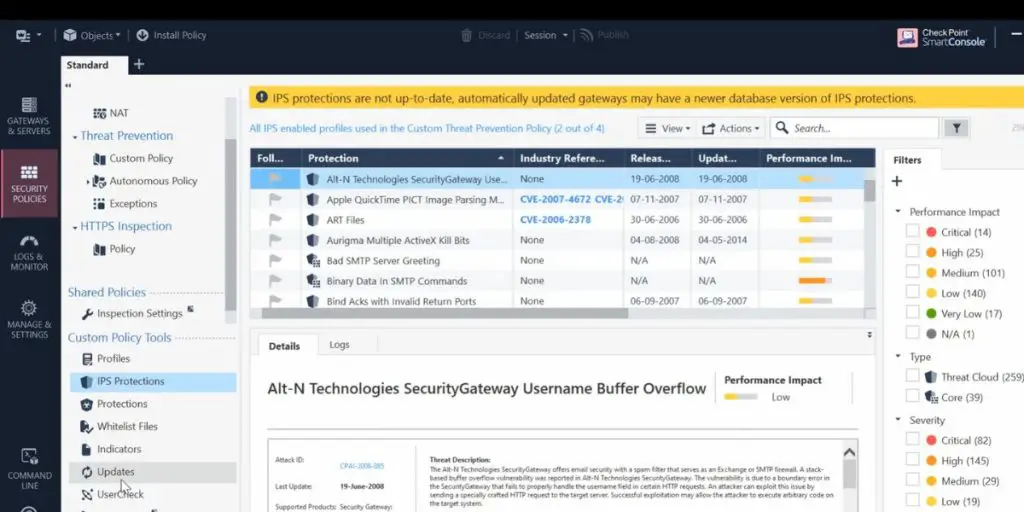
Some screenshots of Check Point IPS
 Likes
Likes
- Suitable for all types of businesses like small, mid-sized, and enterprise
- Supports many industries like retail, financial services, healthcare, government, service provider, education, etc
- It provides acceleration technology to enable IPS safety.
Supported industries
- Retail
- Financial Services
- Federal Government
- State & Local Government
- Healthcare
- Telco Service Provider
- Education
User opinion
It is a comprehensive security platform that provides real-time protection against malicious attacks and helps organizations detect and respond to advanced threats.
The Check Point IPS has been designed to detect malicious traffic at the network level and block malicious content from reaching the internal network.
2. Palo Alto Network
Palo Alto Networks is a leading provider of cybersecurity solutions. Their intrusion prevention system (IPS) provides advanced threat protection from malicious activities on corporate networks, such as Trojans and viruses, and blocks threats at application and network layers.
Features
- Advanced threat protection
- Zero-day exploit prevention
Some screenshots of Palo Alto Network
 Likes
Likes
- Provides detailed visibility into network traffic
- Provides in-depth support
- Provides all features with TP license
- Improves cyber hygiene
 Dislikes
Dislikes
- The software is complex and difficult to manage.
- Many layers of policies and rules existed in different configuration areas and were difficult to find.
- Not user-friendly for common users
- Renewal of license is not so easy
Supported industries
- Public Sector
- Financial Services
- Manufacturing
- Healthcare
- Small & Medium Business Solutions
User opinion
Palo Alto Networks enables customers to identify threats quickly and respond more effectively. The IPS also integrates with other security systems for even greater levels of protection. Still, its license renewal is complex, and software is challenging for common users.
3. CISCO Secure IPS (NGIPS)
Cisco NGIPS is a powerful intrusion prevention system with advanced threat detection and prevention capabilities to help keep your network safe. This next-generation IPS provides real-time visibility into threats, application traffic, and user activity on wired and wireless networks.
Features
- Device-level OS visibility
- Up-to-date security policy
- Flexible deployment options
- Good integration
- High-performance appliances
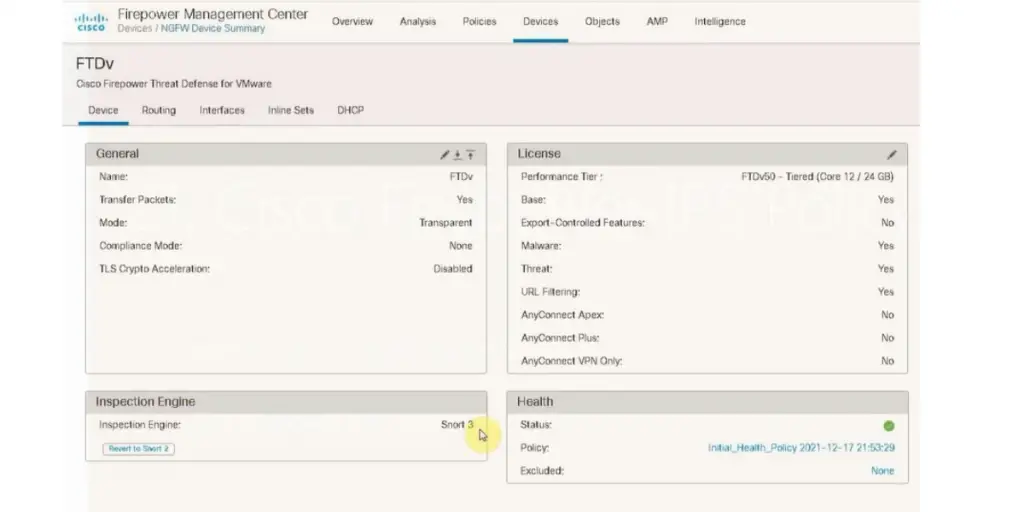
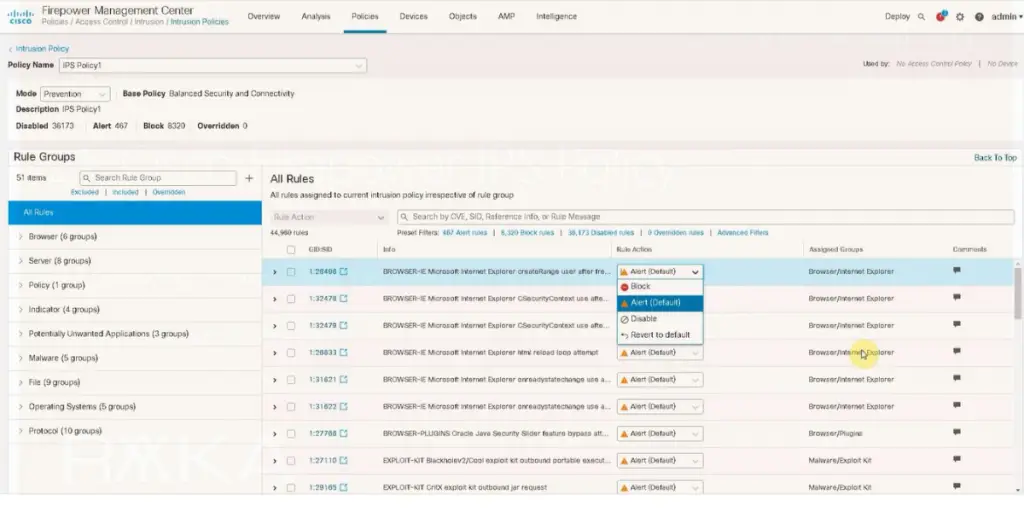
Some screenshots of CISCO
 Likes
Likes
- Provides good technical support
- Allows you to View signs of compromise, host profiles, file trajectory, sandboxing, and vulnerability information
- It enhances operational efficiency
 Dislikes
Dislikes
- Reporting and documentation are not good
- Sometimes, signature rules will fail to protect the vulnerability attack
- Impacts network performance by blocking legit traffic flow
User opinion
Cisco NGIPS offers comprehensive protection with intelligent access control, data filtering and analysis, risk assessment, automated logging, quarantine of infected machines, and automatic updates to ensure continuous protection from the latest threats. Allows you to fine-tune your network security.
4. Fidelis Network
Fidelis Network is an advanced intrusion prevention system that helps your organization detect, investigate, and respond to cyber threats.
This solution offers comprehensive visibility and real-time network traffic control to protect against known or unknown attacks. It analyzes network traffic to calculate network risks.
Using the IPS tool, Fidelis protects other assets, such as endpoint servers and containers, in an integrated way.
Features
- Advanced threat detection and response
- Data security
- Network defense over communication paths
- Real-time and retrospective network analysis
- Proactive cloud and on-premise network defense
Some screenshots of Fidelis Network
 Likes
Likes
- Provides fast data processing
- Powerful machine learning analytics
- Encrypted traffic analyzation
- Ensures data privacy
Supported industries
- Defense
- Healthcare
- Government
- Finance
- Information technology
- Education
- Retail
- Tribal and Gaming
User opinion
Fidelis Network provides automated threat detection and response capabilities across multiple networks, including physical, virtualized, cloud-based, and hybrid environments. It also analyzes data from servers, mobile devices, and endpoints to give you a full view of the attack surface so you can prevent future incidents.
5. Trend Micro Tipping Point IPS
Cyber security provider Trend Micro offers TippingPoint solutions to protect against the most advanced cyber threats.
TippingPoint is a network security system that protects against Zero Day and known vulnerabilities. In addition, trend Micro TippingPoint can track outbound and vertical traffic and block threats in real-time.
As a result, administrators have a greater opportunity for security protection and analysis by monitoring an organization’s security posture.
Features
- Threat intelligence
- Threat protection system
- Centralized management and response
Likes
- Allows you to create a customized traffic management
- Uses machine learning functionalities to provide security against threats
Dislikes
- Some performance issues. When the network load becomes high, the performance will reduce
- Less support in the documentation part
- Dashboard performance issue
- Lack of follow-up features
User opinion
TippingPoint intrusion prevention system protects businesses from malicious attacks. It features advanced threat protection, real-time monitoring and response, automated incident response capabilities, and customizable rules to detect the latest threats better.
6. Hillstone Network Intrusion Prevention System (NTPS)
Hillstone Network provides an integrated security solution to protect modern hybrid infrastructures. It provides advanced intrusion detection and prevention system with flexible deployment options.
In addition, Hillstone Edge Protection offers various edge-protection products, including industry-recognized Hillstone NGFW devices and splinted network penetration prevention systems (NIPS) appliance products.
Features
- Comprehensive protection
- Flexible deployment model
- Context awareness for intelligent and precise targeting
- Smooth integration with Hillstone suites
Some screenshots of Hillstone
 Likes
Likes
- Comprehensive protection range with 2 to 7 layers
- Simple and easy to use
 Dislikes
Dislikes
- It does not provide specific technical training
Supported industries
- Enhancing Security in Higher Education
- Defending Government Agencies
- Fortifying Financial Services
- Safeguarding Telcos and ISPs
User opinion
Hillstone Network Intrusion Prevention System (IPS) is an advanced solution that provides threat detection, prevention, and remediation of malicious activity. It leverages machine learning algorithms to identify suspicious network traffic and recognize and block malicious code.
7. NSFOCUS Next-generation intrusion prevention system
NSFOCUS has a diversified technology offering that combines security technologies, network intelligence, and application protection. Its advanced persistent threat protection protects your business by preventing breaches and blocking intrusions.
Features
- Comprehensive threat protection
- Networking and security features
- Scalable protection with industry-leading performance
- Simplified threat management
 Likes
Likes
- Identifies known and zero-day APTs
- Uses AI with state-of-the-art threat intelligence to identify malicious sites
- Integrates traffic prioritization and DDoS protection to ensure bandwidth availability
User opinion
NSFOCUS Next-Generation Intrusion Prevention System (NGIPS) is an advanced security solution offering comprehensive threat protection by combining intrusion prevention, threat intelligence, and virtual sandboxing.
In addition, it employs AI-powered anomaly detection to detect malicious activities and deep packet inspection to identify and block potential threats at the network level.
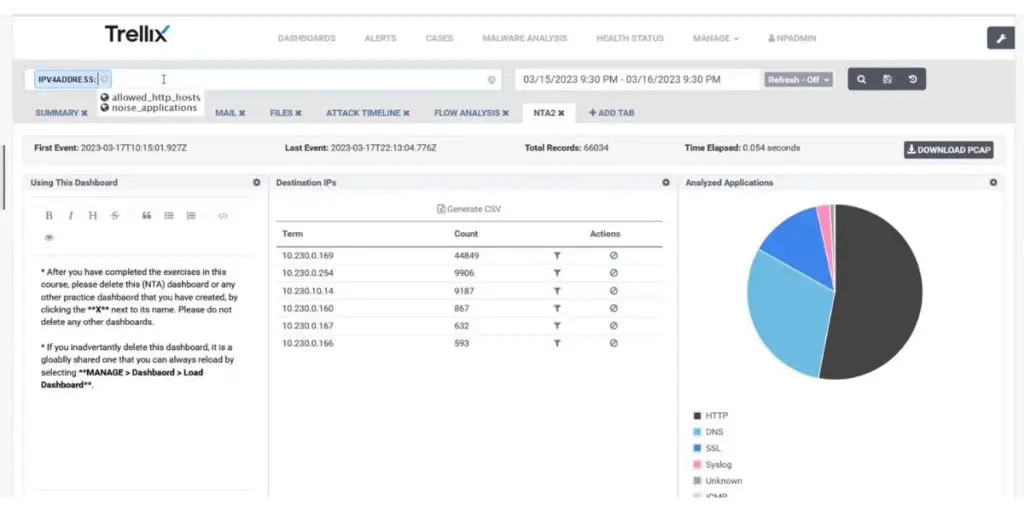
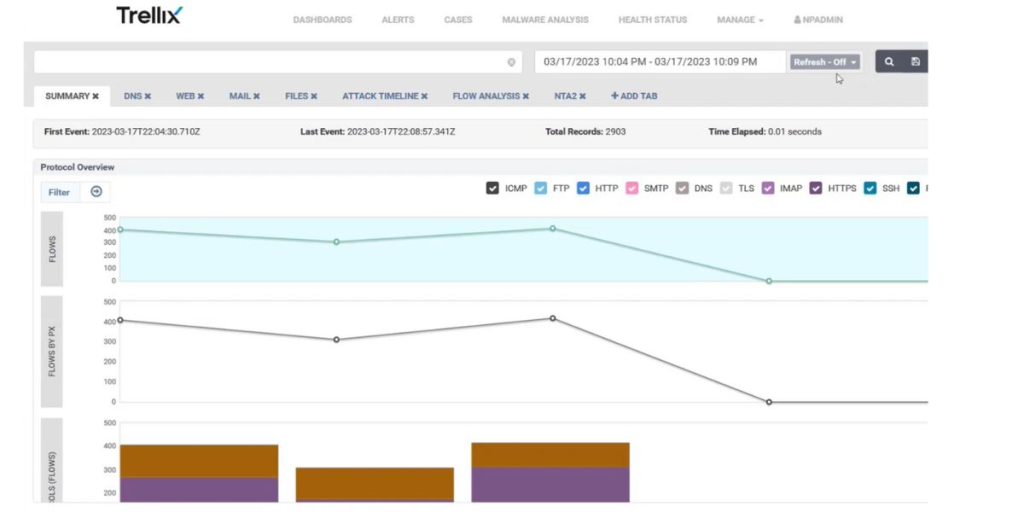
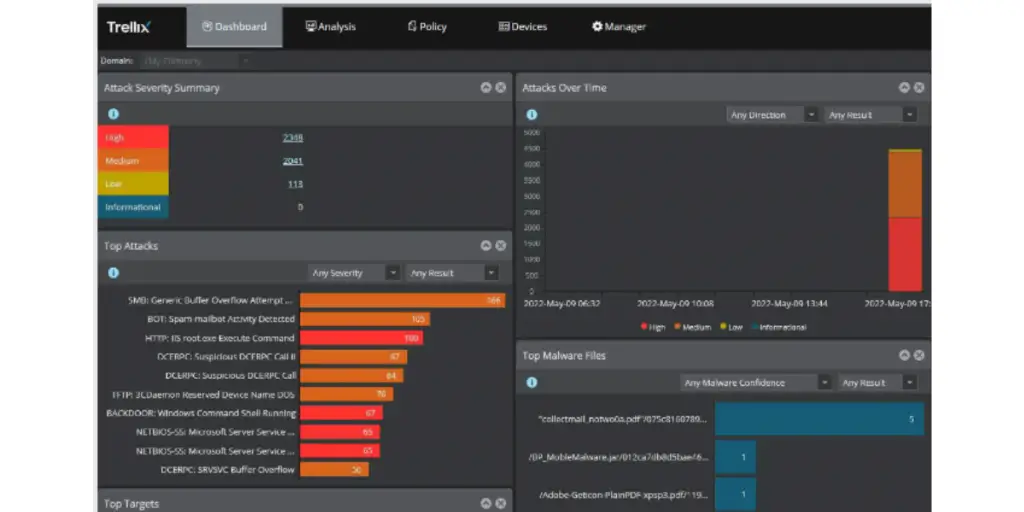
8. Trellix
Trellix IPS is a comprehensive solution that protects networks and systems from new and unknown with a signature-based intrusion prevention system. It combines rules-based security with advanced machine learning, allowing it to detect even the most sophisticated attack attempts.
Features
- Extend botnet intrusion detection and network analysis
- Flexible deployment options
- Treat correlation and context
- Virtual network visibility
- Inspection of network traffic
 Likes
Likes
- It provides an alert prioritizing option
- It Supports network virtualization across private and public cloud platforms.
 Dislikes
Dislikes
- Sometimes you will be alerted by a false alarm.
- Complex user interface and dashboards
User opinion
Trellix IPS has several levels of protection and can be customized to meet your security needs. It finds malicious network traffic and prevents them if no signatures exist with the help of signature-less intrusion detection. Trellix IPS provides an effective layer of defense for any business or organization looking to protect its data from cyber criminals and other external threats.
9. ZScalar Cloud IPS
ZScalar Cloud IPS is an advanced intrusion prevention system that uses techniques like machine learning and artificial intelligence to protect cloud-based applications.
It provides real-time protection against malicious attacks and helps detect suspicious behavior before it can cause damage.
Features
- Unlimited capacity
- Full SSL inspection
- Full integration for context awareness
- Treat intelligence
- Transparent updates
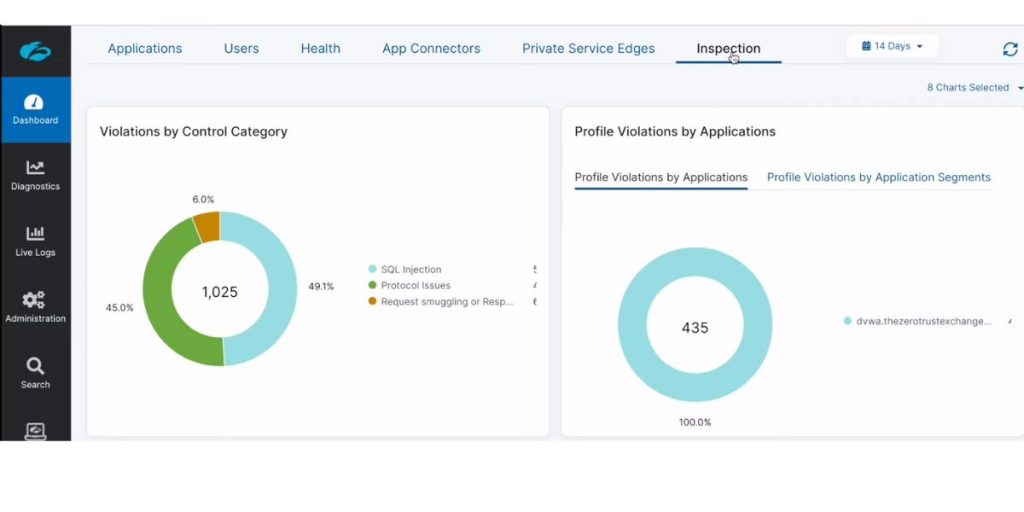
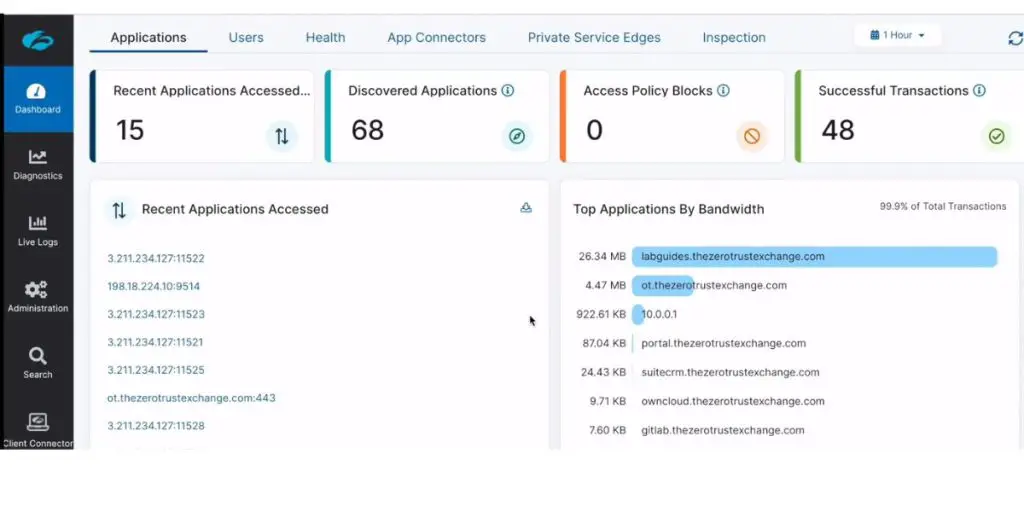
Some screenshots of ZScalar Cloud IPS
 Likes
Likes
- Easily installable software
- It will update itself for the latest threat.
 Dislikes
Dislikes
- The software could be more scalable.
- Customer support response time is longer.
- The on-premise option is not available.
User opinion
ZScalar Cloud IPS offers multi-factor authentication, two-factor authentication, access control rules, vulnerability assessment, and data leakage prevention, among other features, to ensure the highest level of security for your cloud environment. In addition, the latest signature coverage will update automatically and transparently, which helps to avoid change control outages.
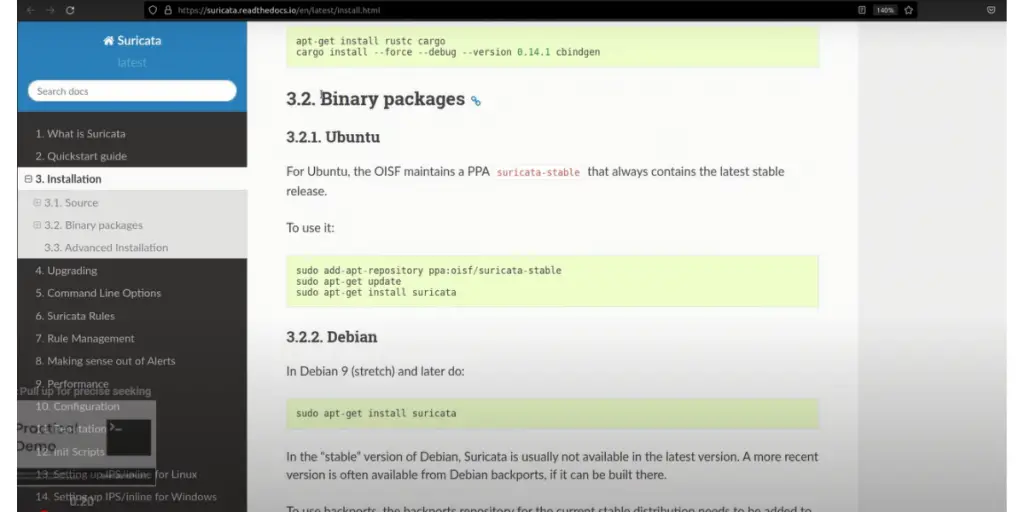
10. SURICATA
Suricata is an open-source intrusion prevention system (IPS) that provides real-time network security monitoring.
It utilizes signature and anomaly detection engines to detect malicious activities, including malware infections, buffer overflows, and scan attempts.
The latest stable release is 6.0.10. Released on 31 January 2023.
Features
- Threat detection and response
- Seamless integration
- PCAP recordings
- IDS alerts
- Protocol transactions
 Likes
Likes
- Forever open-source network security monitoring solution
- Free to use, supported by nonprofit organizations
 Dislikes
Dislikes
- Support resources are less
User opinion
Suricata is an open-source solution supported by the Open Information Security Foundation (OISF). It offers various automated features for particular traffic events, such as inbound/outbound Scans, DDoS protection, and Network Protocol Anomaly Detection. In addition, it logs HTTP requests and logs and stores TLS certificates.
FAQs
What types of cyber attacks are prevented by IPS?
IPS prevents various types of cyber attacks by analyzing network traffic and identifying and responding to potential threats. Some of the attacks that IPS can prevent include
1. Malware attacks – These prevent malware from sneaking into a network by analyzing incoming traffic and blocking suspicious files or downloads. It prevents malware from spreading within the network by isolating infected machines.
2. Denial-of-service (DoS) attacks – It prevents DoS attacks by blocking incoming traffic, sending an overly large number of requests to the network, thus preventing the network from being overwhelmed and causing downtime.
3. SQL injection attacks – It filters incoming traffic and detects attempts to inject malicious code into SQL statements.
4. Cross-site scripting (XSS) attacks – It prevents XSS attacks by analyzing incoming traffic and detecting any attempts to exploit vulnerabilities in web applications.
5. Zero-day attacks – It uses advanced threat intelligence and ML algorithms to detect and respond to new and emerging threats in real-time.
Note: All the above software have not mentioned pricing details on their official sites. You need to contact them directly for the pricing details.
Conclusion
Intrusion prevention systems are a vital component of any security plan. Not only do they help protect against malicious actors and cyber threats, but they also provide valuable insights into the current state of your network. With this list as a guide, you can find an IPS solution that meets your needs.
Reference